Identity Governance & Administration , Incident & Breach Response , Security Operations
Breach Aftermath: The Challenge of More Complete Identity Impersonation

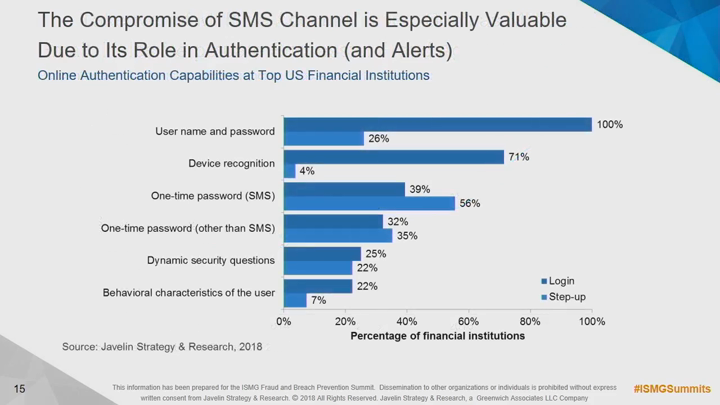
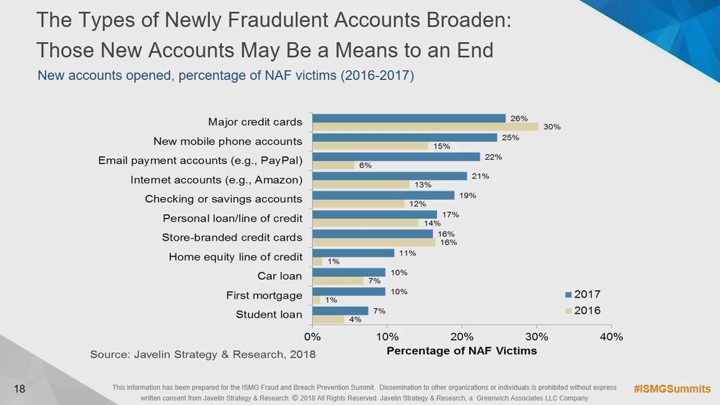
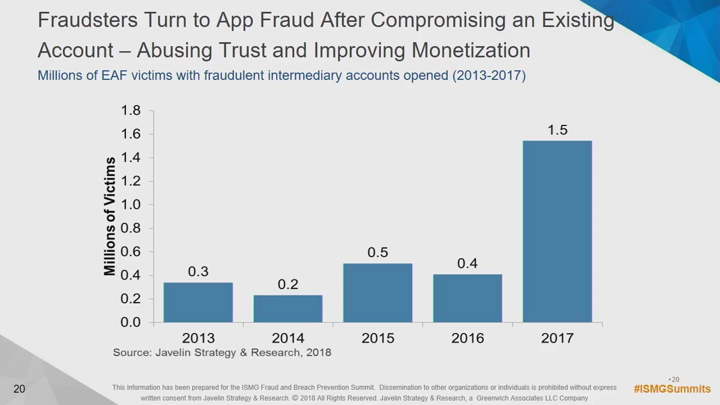
In the wake of Equifax and other major breaches, and armed with all of the personally identifiable information that they will ever need and a keen sense of the security controls that modern organizations use, sophisticated fraudsters are finding success as never before. At the center of it all is a new fraud trend: the practice of impersonating legitimate customers at multiple organizations to further a single fraud scheme. Worse still is that traditional security and fraud tools can't see it and some even help enable it. Attend this session for:
See Also: Case Study: What Elite Threat Hunters See That Others Can't
- Javelin's newest fraud research findings
- How identity impersonation is manifesting, the implications for different organizations such as financial institutions, merchants, and mobile network operators
- What can ultimately be done when a fraudster's version of a consumer is more convincing than the victim's