Endpoint Security , Next-Generation Technologies & Secure Development , Threat Hunting
How to Mature Your Threat Hunting Program
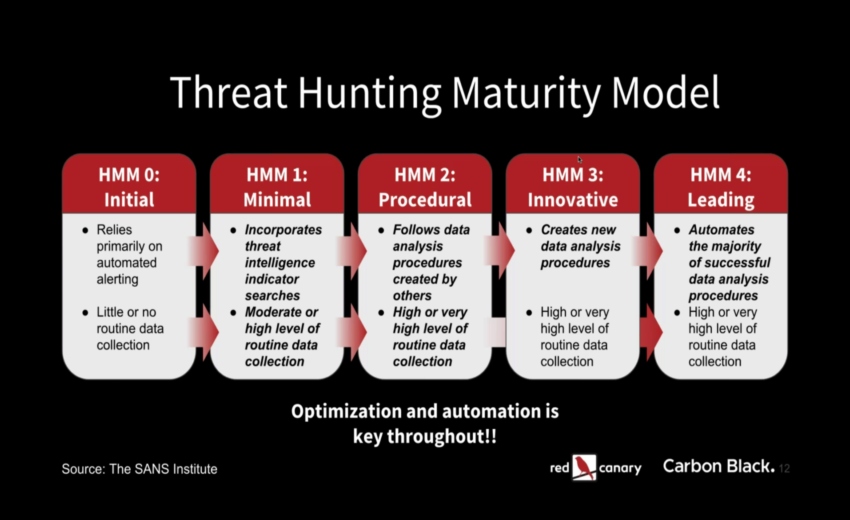
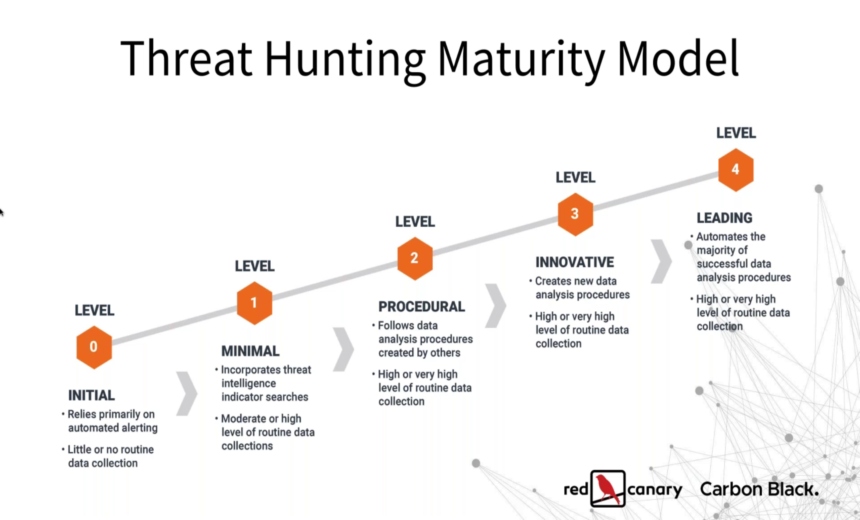
Best practices on using the ATT&CK framework to develop your threat hunting capabilities.Every threat hunt starts with intelligence. As one of the industry's most comprehensive knowledge bases for adversary behavior, ATT&CK provides a structure for hunters to build their hypotheses and search for threats.
Hit play on the video above and learn how to use ATT&CK to:
- Increase the efficacy of your threat hunting program;
- Hunt for adversary tactics and techniques across the ATT&CK matrix;
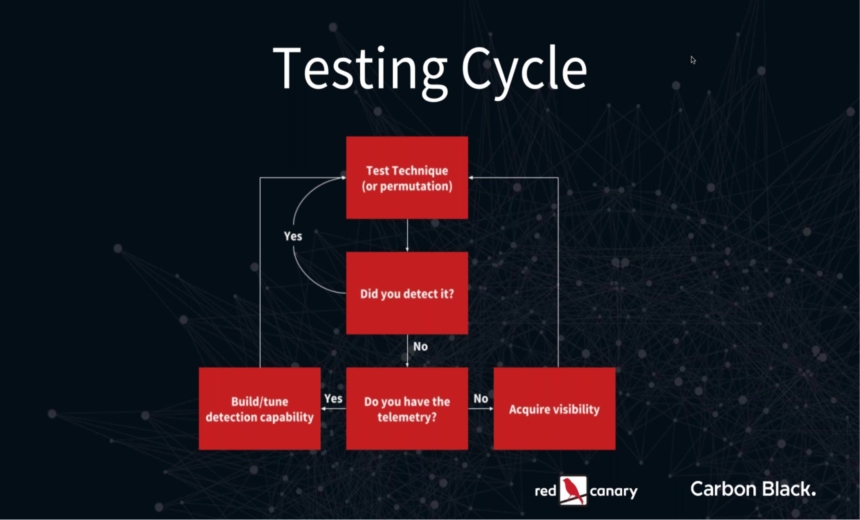
- Develop a hypothesis and test it against known techniques;
- Obtain a broader set of evidence by hunting for adversarial techniques rather than specific signatures.